Ensure simple and secure unified user experience for your IT and employees
80% of all employees use more than one device to remain productive anywhere at anytime. They expect to use the device of their choice and access corporate networks, apps and data intuitively and easily across platforms. For IT this means – more complexity and more risk. Your IT must be enabled to efficiently manage diversity while ensuring that apps and sensitive data are secure.
Why Use Unified Endpoint Management?
Manage all devices in one solution
Reduced costs and reduced burden on your IT. Still full control over all devices, apps and data.
Built-in IT security and compliance
Built-in comprehensive protection for all workspaces. Sensitive data remains secure and compliance is maintained.
Standardized, continuous processes
Complete integration with service and software asset management for better decisions and lower costs.
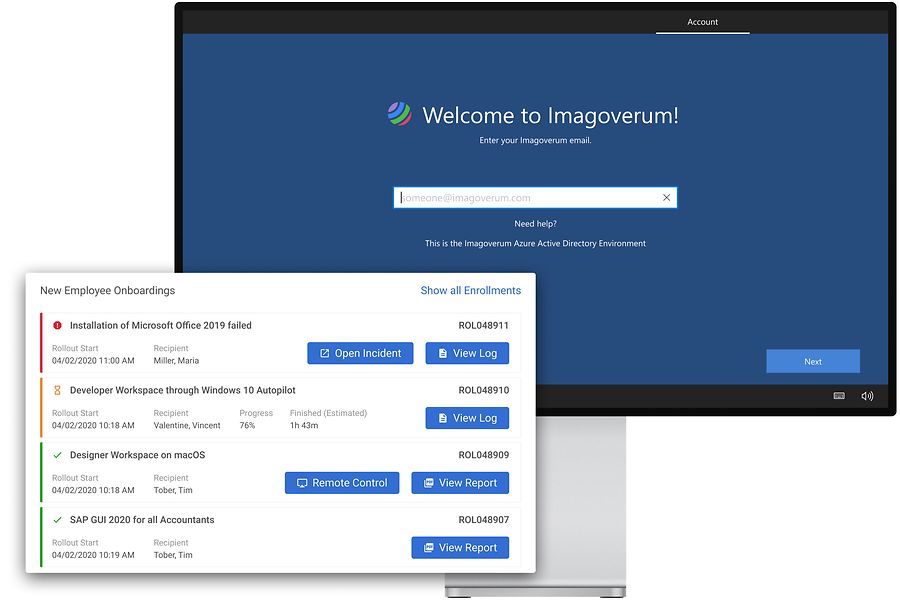
Zero Touch Device Rollout
Ship your devices non-stop to your users and ensure that they’re being setup automatically fully compliant with Windows 10 Autopilot.
- Define your Desired State Configuration – Work backwards from your vision and define how your Workspace shall be configured with just a few clicks to create the perfect Sales Workspace Configuration for example.
- Assign this Configuration to your Users – Your Workspace Configurations including all the profiles, apps and security measures. They just have to be assigned once to the group of users that shall receive it.
- Ship your devices directly to your Users without ever touching them – Now it’s getting super easy – you don’t even have to unwrap the devices anymore. Just ship them to your users, even directly from the vendor and Windows 10 Autopilot will take over when the user powers up the device for the very first time.
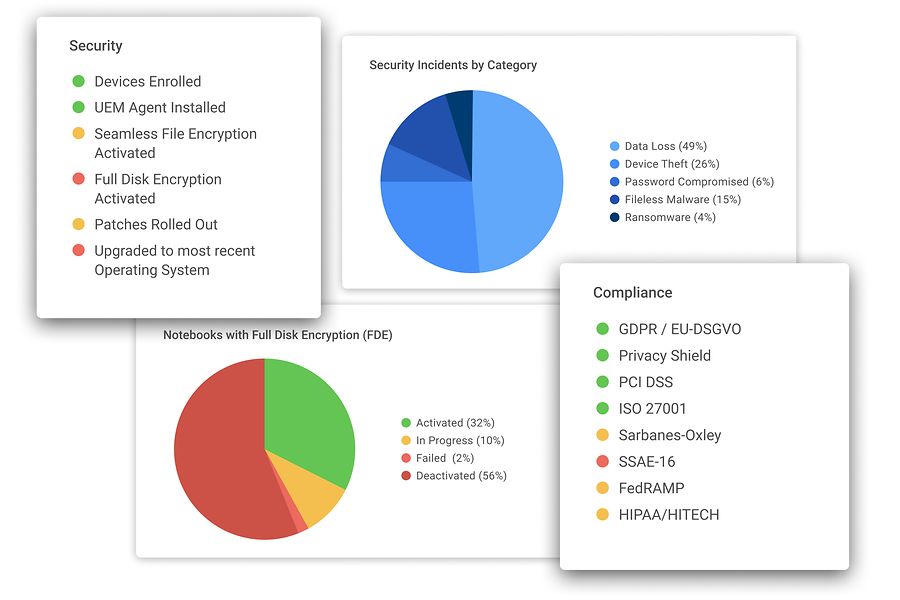
Security built right into your Device Management
Have a single source of truth for everything regarding your endpoints – Configuration, Security, Health.
- All Endpoints in a single Unified User Experience (UUX) – There’s only one place you have to go to inspect, manage and secure all your devices – in any browser, on any device
- Health, state and compliance united – Gain transparency about everything that’s going on and all the changes regarding your infrastructure in a blink
- Remediate automatically with smart actions – Let the system help you to constantly increase the amount of automation and implement counter actions to common issues
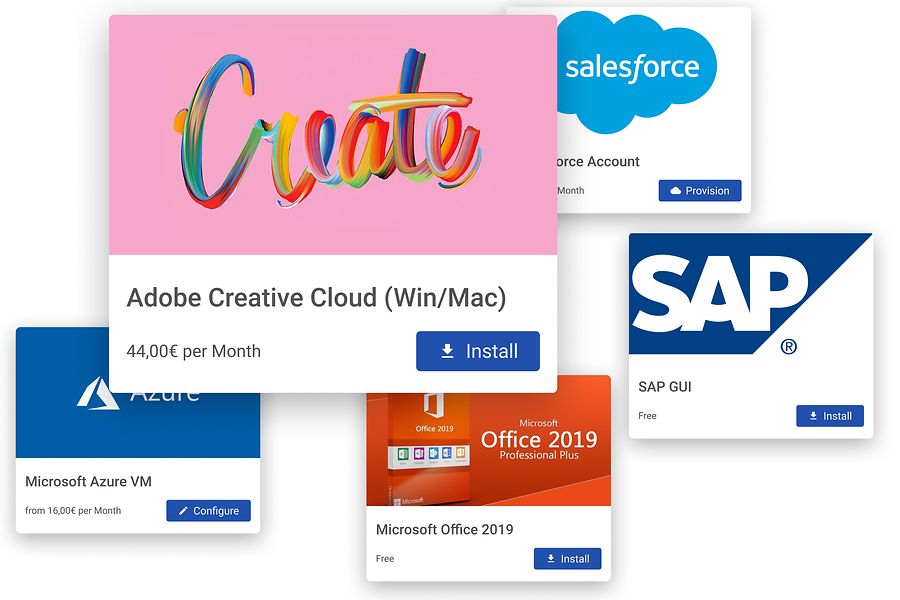
Combine the power of Secure Unified Endpoint Management (SUEM) and Enterprise Service Management (ESM)
Use the out-of-the-box Connectors to automatically bring all your Configurations into your Enterprise Service Management.
- Configure the out-of-the-box Connector – With just a few clicks you can form the link between your Enterprise Service Management (ESM) and Secure Unified Endpoint Management (SUEM)
- All Packages and Configuration will be kept in sync – Everything in your Secure Unified Endpoint Management (SUEM) will be imported into Services in your Service Catalog – ready to be consumed by your users
- Optimize your efforts based on consumption and usage – Stop investing time into updating packages and configurations nobody uses and prioritize based on the actual usage of your packages and configurations
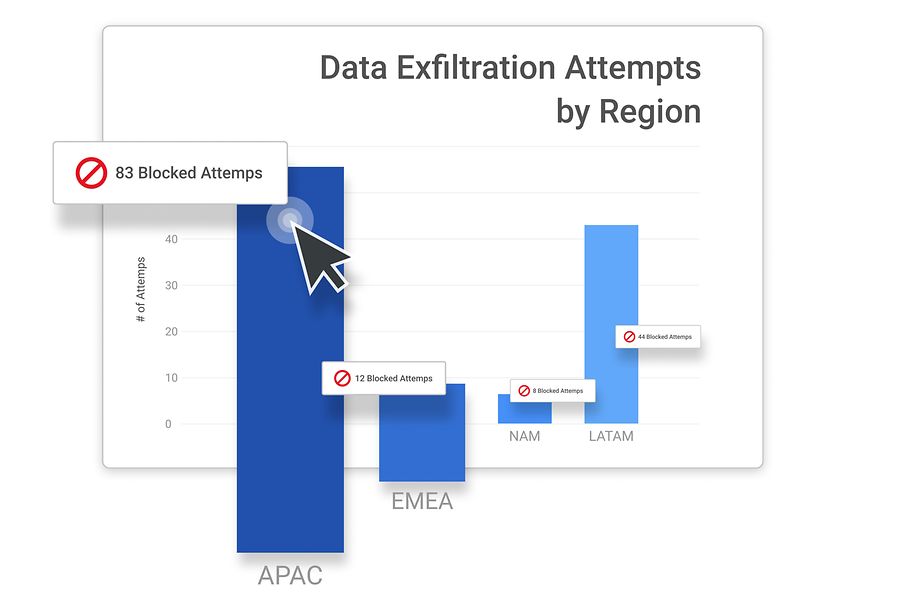
User and Entity Behavioral Analysis (UEBA)
Your data and the productivity of your users are the most critical assets your company has – protect and empower them!
Behavioral Baseline – The system automatically determines a baseline for every employee and endpoint.
Anomaly Detection – If anything out of the ordinary happens, like some endpoint uploading tons of data to an unknown datacenter at Saturday night, the system blocks the attempt in real-time – no harm done.
Security Incident Management – The issue needs to be analyzed and resolved at its root cause. Here’s when Security Incident Management comes into play to decompile the issue and close the leak once and for all.
